Posts by Veridify Security
The Importance of Cybersecurity Protection for Building Infrastructure
Podcast Outline Introduction Understanding Cybersecurity for Building Infrastructure Real-Time Security: A Necessity Smart Buildings: Balancing Innovation and Security Zero Trust Systems: The Future of Cybersecurity Challenges in Securing IoT Devices Implementing Secure Firmware Solutions Conclusion Podcast Transcript Introduction Welcome to another insightful episode of “Protecting Buildings and OT from Cyber Attacks,” where we delve into…
Read MoreCybersecurity Insurance for Buildings, BAS, BMS
Building owners should have cybersecurity insurance for their building automation systems (BAS) due to the increasing risk of cyberattacks on connected infrastructure. Key Reasons for BAS/BMS Cybersecurity Insurance Protection Against Financial Loss: A cyberattack on BAS can result in significant financial losses from system downtime, operational disruptions, or damaged equipment. Cybersecurity insurance can cover the…
Read MoreCybersecurity Awareness Month 2024
October is Cybersecurity Awareness Month 2024 Cybersecurity Awareness Month 2024 is a collaboration between government and private industry to raise awareness about digital security and empower everyone to protect their personal data from digital forms of crime. The Cybersecurity and Infrastructure Agency (CISA) and the National Cybersecurity Alliance partner to create resources and communications for…
Read MoreBuilding Automation Endpoint Protection Is Critical for Cybersecurity
Building automation systems (BAS), now highly-connected to the internet, have transformed how the infrastructure of residential, commercial, and industrial properties is managed and optimized. From heating, ventilation, and air conditioning (HVAC) systems to lighting, security, life safety, and power distribution, these systems are now smart, centralized, and increasingly automated. While this level of convenience and…
Read MoreProtecting Operational Technology from Quantum Computing
Protecting OT from Quantum Computing What is Quantum Computing? Quantum computing leverages the principles of quantum mechanics to perform complex calculations far more efficiently than classical computers. Unlike classical bits, which represent data as 0 or 1, quantum bits (qubits) can exist in multiple states simultaneously due to superposition. This, along with entanglement—where qubits become…
Read MoreZero Trust: Reinforcing Security in Industrial Control Systems
As industrial control systems (ICS) become increasingly digitized, ensuring robust ICS security measures is paramount. In this article, we delve into the concept of Zero Trust and its potential to revolutionize the security landscape for industrial control systems. With cyber threats evolving in complexity and sophistication, traditional security measures are no longer sufficient. Zero Trust…
Read MoreZero Trust for OT Security: Cyber Defense Inside the Perimeter
Inside the Perimeter Defense is a Crucial Part of Defense in Depth for OT Security Firewalls for OT Security Perimeter Defense Firewalls are essential components of network security, acting as perimeter defenses that control incoming and outgoing network traffic based on predetermined security rules. However, they are not without their own set of potential security…
Read MoreModbus Vulnerabilities Used for Cyberattack on a Heating Utility
Heat and Hot Water Disrupted to over 600 buildings, about 100,000 people, for 48 Hours Cyberattack on a Heating Utility A cyberattack on a heating utility (also known as district heating) in the Ukrainian city of Lviv, the largest city in western Ukraine, in January 2024. The malware, named FrostyGoop, is one of the few…
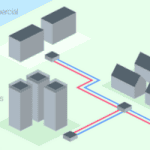
Read MoreProtecting Building OT Systems from Cyber Threats
Operational Technology (OT) systems in buildings, which include HVAC, lighting, access control, and other critical infrastructure, are increasingly becoming targets for cyber threats. The rise in attacks on these systems underscores the importance of robust cybersecurity measures to protect them. Here’s a look at how to safeguard building OT systems from cyber threats. Understanding the…
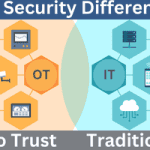
Read MoreKey Differences Between Zero Trust OT Security and Traditional IT Security
How is Zero Trust for OT Security Different from Traditional IT Security? Zero Trust for operational technology (OT) security differs significantly from traditional IT security models in several ways. Here are some key differences: Security Method Traditional IT Security Zero Trust OT Security Trust Model – Assumes that everything inside the network can be trusted.…
Read More