Posts by Veridify Security
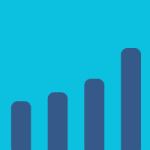
Monetary Damage of Reported Cybercrime in the US from 2001-2022
Growth in Cybercrime Cybercrime is not just a threat to data and privacy; it also comes with a significant monetary cost. The monetary damage of reported cybercrime in the United States grew steadily from 2001-2017, and then accelerated starting in 2018. There was a year-over-year increase of around 50 percent from 2021 to 2022. Since…
Read MoreBACnet Security Issues and How to Mitigate Cyber Risks
BACnet is a commonly used protocol for building automation and operational technology (OT) systems, and is used to establish communication between various devices in a network. Because BACnet-based building systems were originally deployed in isolated (air-gapped) environments, BACnet was not designed with security. Therefore, millions of BACnet devices are lacking common security mechanisms such as…
Read MoreImproving BACnet Secure Connect (BACnet/SC) Deployment with Automated Certificate Management
Managing BACnet Secure Connect (BACnet/SC) certificates can be a challenging task, especially for large buildings. Just recently at the AHR Expo 2024, we learned of a project that had over 300 devices and the decision was made to use 10-year certificates due to the multiple days (3-4) of labor needed to deploy BACnet/SC certificates. The…
Read MoreBACnet MS/TP Security Risks and Vulnerabilities
What is BACnet MS/TP? BACnet MS/TP (Master-Slave/Token-Passing) is a widely used communication protocol in building automation and control systems. BACnet MS/TP is implemented with a shared bus and one or more building control devices daisy-chained along the wiring from a controller or a BACnet IP router/gateway. It is commonly used to connect field devices such…
Read MoreSmart Building Cybersecurity Best Practices
Key Points Smart buildings integrate interconnected systems like HVAC, lighting, access control, and more to optimize efficiency, sustainability, and occupant comfort through centralized, automated operations. Security challenges arise from inherently unsecure communication protocols, increased connectivity, and remote/cloud access, expanding the cyberattack surface and exposing systems to threats like unauthorized access and data breaches. Key security…
Read MoreAHR Expo 2024 Event Preview
Veridify Security will be exhibiting at the AHR Expo 2024 in booth S6174. Our demo is getting assembled and being prepared to be shipped to Chicago! Verdify will be exhibiting a live demo of DOME™, a building automation cybersecurity platform that protects both new and existing building automation devices. The newly revised demo platform will…
Read MoreThe Hack of Marconi’s 1903 Wireless Demonstration
In the annals of technological history, the year 1903 stands as a pivotal moment in the progression of wireless communication. Guglielmo Marconi, the visionary inventor and pioneer of wireless telegraphy, was set to showcase his groundbreaking technology to the world. Little did he know that this momentous occasion would be marred by an unexpected and…
Read MoreEmbracing Digital Transformation – Zero Trust with Operational Technology
Embracing Digital Transformation – Zero Trust with Operational Technology Episode #175: In this episode titled “Embracing Digital Transformation – Zero Trust with Operational Technology” by Darren Pulsipher, Chief Solution Architect for Public Sector at Intel, interviews the CEO and Founder of Veridify Security Louis Parks. They discuss the unique problems with Operational technology networks that…
Read MoreZero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS/OT/SCADA)
Watch this webinar replay of “Zero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS /OT/SCADA)” to learn about applying zero trust security at the device level. This webinar addresses the following topics: ICS cybersecurity standards Existing ICS security approaches Zero Trust and device-level implementation Cybersecurity for existing ICS devices Zero Trust…
Read MoreHow to Conduct a Cybersecurity Risk Assessment for Smart Buildings
Key Points Understand the Smart Building Ecosystem: Recognize the interconnected components—IoT devices, BMS, access control, and sensors—that enhance operations but also introduce cybersecurity vulnerabilities. Perform a Structured Risk Assessment: Define system assets and boundaries, identify threats and vulnerabilities (internal and external), evaluate impact and likelihood, and assign risk levels to prioritize mitigation. Implement Mitigation and…
Read More