BACnet MS/TP Security Risks and Vulnerabilities
What is BACnet MS/TP?
BACnet MS/TP (Master-Slave/Token-Passing) is a widely used communication protocol in building automation and control systems. BACnet MS/TP is implemented with a shared bus and one or more building control devices daisy-chained along the wiring from a controller or a BACnet IP router/gateway. It is commonly used to connect field devices such as sensors, actuators, and controllers in building automation systems.
Key features of BACnet MS/TP include:
- Master-Slave/Token-Passing: The MS/TP protocol uses a master-slave (MS) architecture, where one device (the master) controls communication and coordinates access to the network. Token-passing (TP) is used to regulate access to the network, ensuring that only one device transmits data at a time to avoid collisions. This method of operation may also be referenced as client-server where the client is the controlling device.
- Twisted Pair Communication: BACnet MS/TP uses a twisted pair cable for communication, which is cost-effective and suitable for shorter distances typically found in building automation applications.
- Speed and Reliability: MS/TP is designed for reliable communication in building automation environments, with a typical baud rate of 9600 or 38400 bits per second (bps). The protocol includes error checking and retransmission mechanisms to ensure data integrity. The communication speed is far below that of Ethernet and BACnet/IP.
- Limited Network Size: Due to the nature of token passing, BACnet MS/TP networks are typically limited in size, with a maximum recommended number of devices ranging from 32 to 256, depending on the baud rate and network topology. Generally, the more devices that are on a network, the slower the response. Wiring limitations also contribute to limiting the number of devices on a BACnet MS/TP segment.
- Compatibility: BACnet MS/TP is part of the BACnet standard and is widely supported by building automation equipment manufacturers. This ensures interoperability between devices from different manufacturers within a BACnet MS/TP network. Additionally, BACnet MS/TP devices can communicate to BACnet/IP devices through a BACnet router.
BACnet MS/TP Scalability
The maximum number of BACnet MS/TP devices allowed is 128 on the same bus. However, the number of devices that can be connected to a single bus depends on various factors including:
- Baud Rate
- Cable length
- Device responsiveness
- Device type and function
In practical terms, BACnet MS/TP networks commonly support a moderate number of devices, often ranging from a few to several dozen. The more devices on a bus, the more mistakes that can be made during installation and the harder it is to troubleshoot where a fault is located. Many new BACnet installations use a hybrid network design with BACnet IP (Ethernet) used between floors as a backbone, and BACnet MS/TP trunks used on each floor. The use of BACnet IP as backbone allows for increased communication range through one or more Ethernet switches, reduced physical ports at controllers, and scalability by aggregating multiple smaller MS/TP segments.
BACnet MS/TP Security Risks
While BACnet provides interoperability and facilitates communication between devices, it is important to be aware of potential security risks associated with BACnet MS/TP. Here are some key security risks:
Lack of Encryption: BACnet MS/TP lacks native encryption, which means that data transmitted over the network is not automatically protected. This absence of encryption can expose sensitive information to eavesdropping or tampering.
No Authentication Mechanisms: BACnet MS/TP has no built-in authentication mechanisms, allowing potential attackers to gain unauthorized access to devices on the network. Lack of authentication can lead to unauthorized control and manipulation of building systems. Without authentication, a “good” device can be replaced with a “bad” device, or a “bad” device can just be added to the network.
Vulnerability to Physical Attacks: BACnet MS/TP relies on a physical wiring scheme, and the network is susceptible to physical attacks. Unauthorized access to the wiring or tampering with devices can compromise the integrity of the communication.
Token-Passing Mechanism Vulnerabilities: The token-passing mechanism used in BACnet MS/TP can introduce vulnerabilities. If an attacker gains control of the token, they may have the ability to control or disrupt communication within the network.
Broadcasting of Messages: BACnet MS/TP uses broadcasting for communication, which means that messages are sent to all devices on the network. This can lead to security issues such as unauthorized devices intercepting sensitive information.
Lack of Segmentation: In some deployments, BACnet MS/TP networks may not be adequately segmented, leading to a flat network architecture. Without proper segmentation, a compromise in one part of the network can potentially affect the entire system.
Device Vulnerabilities: Devices that implement the BACnet MS/TP protocol may have their own vulnerabilities. If these vulnerabilities are exploited, it can compromise the security of the entire building automation system. As security standards evolve, devices using BACnet MS/TP may lag in adopting the latest security measures, leaving them further vulnerable to emerging threats.
Unauthorized Device Addition: BACnet MS/TP networks may be susceptible to unauthorized devices being added to the network. Without proper access controls and device authentication, attackers may introduce malicious devices into the network.
Difficulty in Monitoring and Logging: Monitoring and logging capabilities in BACnet MS/TP may be limited. Lack of comprehensive monitoring can make it challenging to detect and respond to security incidents in a timely manner.
BACnet MS/TP Vulnerability Risk Mitigation
Addressing these security risks requires a multi-faceted approach that includes implementing encryption, securing physical access, enforcing strong authentication, segmenting networks, and keeping devices and software up to date with security patches. Security practices should align with industry standards and guidelines to ensure robust protection of BACnet MS/TP-based building automation systems. Regular security assessments and audits are also essential to identify and mitigate potential vulnerabilities.
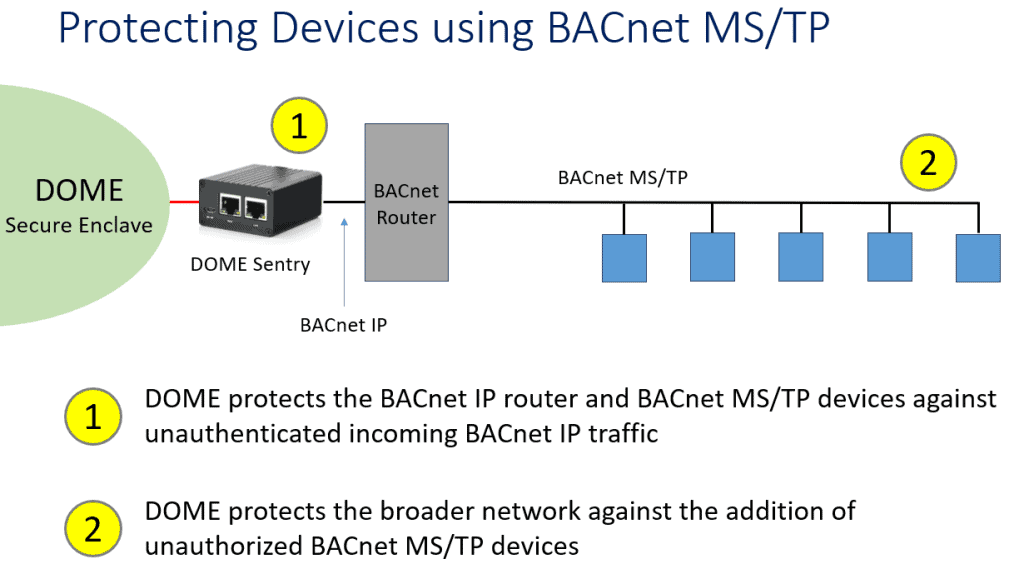
BACnet SC (Secure Connect) and platforms like Veridify’s DOME are solutions that can be used to provide cybersecurity for BACnet IP devices. DOME provides some unique benefits when providing cybersecurity for BACnet MS/TP devices when they are connected through a BACnet IP router/gateway.
1. DOME protects the BACnet IP router and BACnet MS/TP devices against unauthenticated incoming BACnet IP traffic
2. DOME protects the broader network against the addition of unauthorized BACnet MS/TP devices
Conclusion
BACnet MS/TP has numerous security risks for which some forms of cyber risk mitigation is possible. DOME provides unique additional security for BACnet MS/TP devices to protect against unauthorized communication from devices on the IP network, and to prevent unauthorized devices added to a BACnet MS/TP trunk from communicating to the BACnet IP network.
Learn More about DOME for BACnet MS/TP security: Contact Us | Request a Demo
—
Blog Post Summary – All of our posts listed on one page back through 2019
See the slides below to learn more about cybersecurity for building controls and smart buildings:
Keywords: BACnet MS/TP security,