Benefits of Zero Trust for OT Cybersecurity
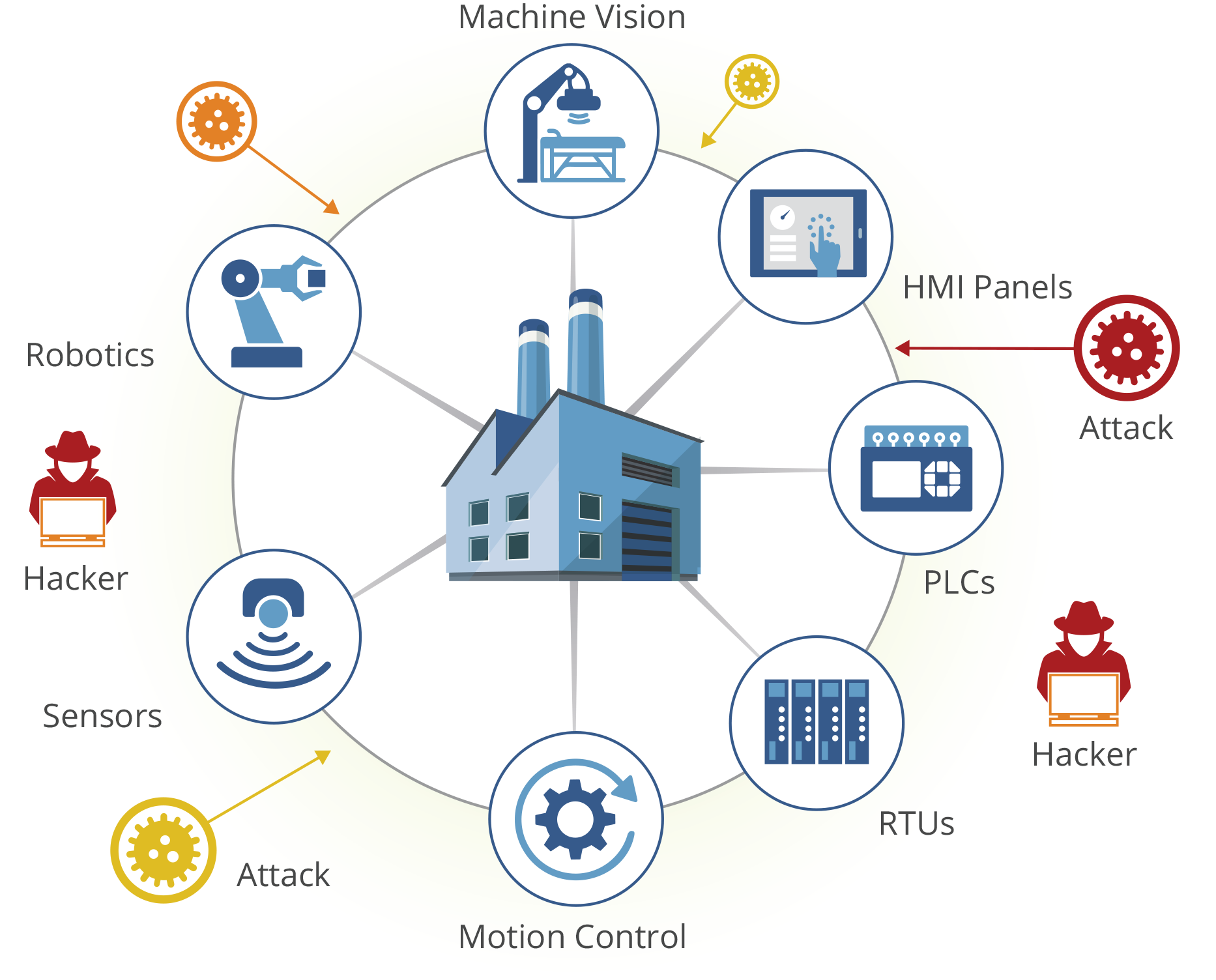
Operational technology (OT) refers to the hardware and software systems that are used to control and monitor physical devices, processes, and events in an organization. These systems are critical to the functioning of many industries, including manufacturing, energy, transportation, and utilities.
In recent years, there has been an increased focus on securing OT systems due to the potential consequences of cyber attacks. A successful attack on an OT system can result in physical damage to equipment, financial loss, and even loss of life.
Breach discovery is when the organization becomes aware that the incident occurred. According to IBM, it takes a company 197 days to discover the breach and up to 69 days to contain it.
One approach to securing OT systems is the concept of zero trust. Zero trust is a cybersecurity model that assumes that all network traffic is untrusted and that all users and devices must be authenticated and authorized before they are granted access to resources.
There are several benefits to implementing a zero trust model for OT cybersecurity:
- Improved security – A zero trust model assumes that all network traffic is untrusted and requires authentication and authorization before granting access. This means that even if an attacker gains access to the network, they will not be able to access sensitive resources unless they have the necessary credentials.
- Enhanced visibility – Implementing a zero trust model can provide greater visibility into network activity and identify unusual or suspicious behavior. This can help organizations detect and respond to potential threats more quickly.
- Simplified compliance – Many industries have strict regulations for securing OT systems. A zero trust model can help organizations meet these requirements by providing a clear and consistent method for controlling access to resources.
- Reduced risk of insider threats – Insider threats, such as employees who intentionally or unintentionally compromise security, can be a significant risk to OT systems. A zero trust model can help reduce this risk by requiring all users to be authenticated and authorized before they are granted access to resources.
- Increased agility – A zero trust model can help organizations respond more quickly to changing business needs by allowing them to easily add or remove access to resources for specific users or devices.
A zero trust model can be implemented as an overlay or embedded solution with Veridify’s DOME platform to provide cybersecurity for industrial automation and SCADA devices. Devices such as controllers, PLCs, actuators, sensors, and transmitters, can all be enabled with real-time protection to stop cyber attacks, which is superior to just reporting that an anomaly has occurred.
The benefits of a zero trust model for OT cybersecurity are significant. By assuming that all network traffic is untrusted and requiring authentication and authorization before granting access, organizations can improve security, simplify compliance, and reduce the risk of insider threats.Top of FormBottom of FormTop of Form
Contact Veridify to learn about implement an OT cybersecurity solution for your organization.