Cybersecurity
AHR Expo 2024 Event Preview
Veridify Security will be exhibiting at the AHR Expo 2024 in booth S6174. Our demo is getting assembled and being prepared to be shipped to Chicago! Verdify will be exhibiting a live demo of DOME™, a building automation cybersecurity platform that protects both new and existing building automation devices. The newly revised demo platform will…
Read MoreThe Hack of Marconi’s 1903 Wireless Demonstration
In the annals of technological history, the year 1903 stands as a pivotal moment in the progression of wireless communication. Guglielmo Marconi, the visionary inventor and pioneer of wireless telegraphy, was set to showcase his groundbreaking technology to the world. Little did he know that this momentous occasion would be marred by an unexpected and…
Read MoreEmbracing Digital Transformation – Zero Trust with Operational Technology
Embracing Digital Transformation – Zero Trust with Operational Technology Episode #175: In this episode titled “Embracing Digital Transformation – Zero Trust with Operational Technology” by Darren Pulsipher, Chief Solution Architect for Public Sector at Intel, interviews the CEO and Founder of Veridify Security Louis Parks. They discuss the unique problems with Operational technology networks that…
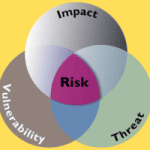
Read MoreHow to Conduct a Cybersecurity Risk Assessment for Smart Buildings
As smart buildings are becoming increasingly prevalent, the integration of advanced technologies into the infrastructure of these structures introduces a myriad of cybersecurity risks. Conducting a comprehensive cybersecurity risk assessment is imperative to identify potential threats, vulnerabilities, and safeguard the integrity of smart building systems. This blog post will explore key steps and considerations involved…
Read MoreCybersecurity Awareness Month 2023
October is Cybersecurity Awareness Month 2023 Cybersecurity Awareness Month 2023 is a collaboration between government and private industry to raise awareness about digital security and empower everyone to protect their personal data from digital forms of crime. The Cybersecurity and Infrastructure Agency (CISA) and the National Cybersecurity Alliance partner to create resources and communications…
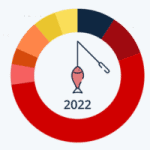
Read MoreShare of Worldwide Cyber Attacks by Type 2022
October is Cybersecurity Awareness Month. While Veridify specializes in cybersecurity for Building Automation, Industrial Controls Systems (ICS/.SCADA), and Critical Infrastructure, we also share in raising awareness for everyone to improve their cybersecurity posture. As the data below indicates, the most prevalent form of cyber crime in 2022 was from phishing attacks. We all see this…
Read MoreBuilding Automation Systems, Smart Buildings, and 5 Ways to Make Them Cyber Secure
Watch this webinar replay of “Building Automation Systems, Smart Buildings, and 5 Ways to Make Them Cyber Secure” to learn about cybersecurity for buildings. Buildings are becoming more connected and more at risk to cyberattacks. This webinar will address the following items: • Connected building trends • Building controls advancements and operating efficiencies • Connected…
Read MoreZero Trust – A Virtual Air Gap for OT Security
Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making,…
Read MoreZero Trust for OT Security – Shields Up vs Damage Report
In the original and newer Star Trek episodes and movies, the captain would order “shields up” or “raise shields” prior to an attack to prevent damage to the USS Enterprise. The shields were some sort of force field of which the physics is never fully described. During or after an attack the captain would request…
Read MoreZero Trust for OT Security – Overcoming Legacy Device Security Gaps and Technical Debt
The proliferation of interconnected Operational Technology (OT) devices in critical infrastructure and industrial sectors has ushered in new opportunities for increased efficiency and automation. However, this digital transformation also brings forth significant cybersecurity challenges. Perimeter security is not a sufficient solution and legacy devices and systems often lack robust security measures, leaving critical infrastructure vulnerable…
Read More