Increased Number of Cyber Exposed OT/ICS Devices
Exposed OT/ICS Devices
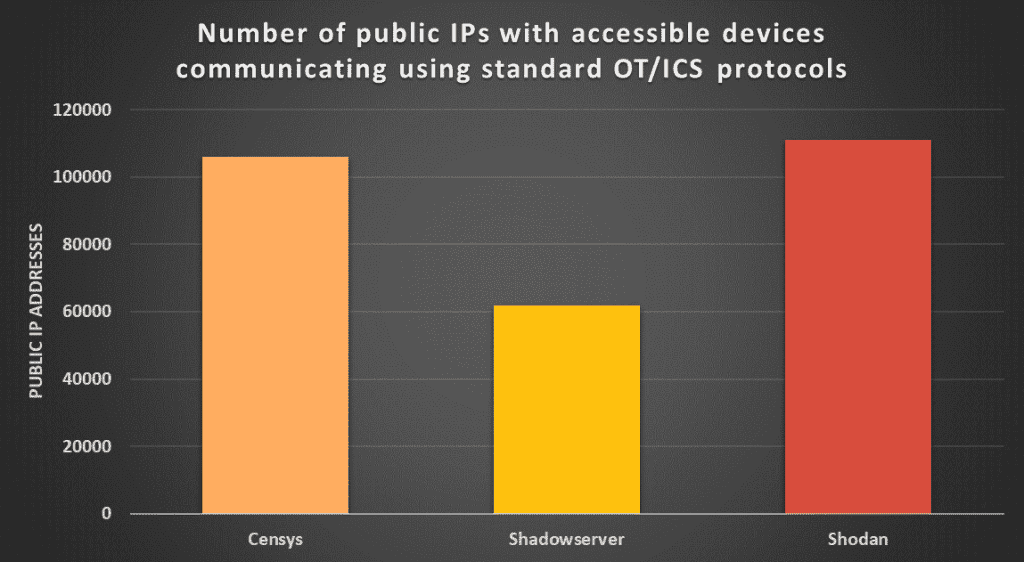
Recent data from several tracking sources indicates there has been an increase in the number of public IP addresses with accessible devices using standard OT/ICS protocols – BACnet, Modbus, Fox, Ethernet/IP, S7, and more. Data from three different sources – Censys, ShadowServer, and Shodan – give insight into the number of publicly exposed IP addresses that have devices using OT/ICS protocols.
The data is different depending on the source, but overall it highlights the problem of exposed OT/ICS devices that can have increased vulnerability to compromise or a cyberattack. Based on this data, there are approximately 60,000 to 110,00 public IP address with devices using OT/ICS protocols.
Source: Sans Internet Storm Center
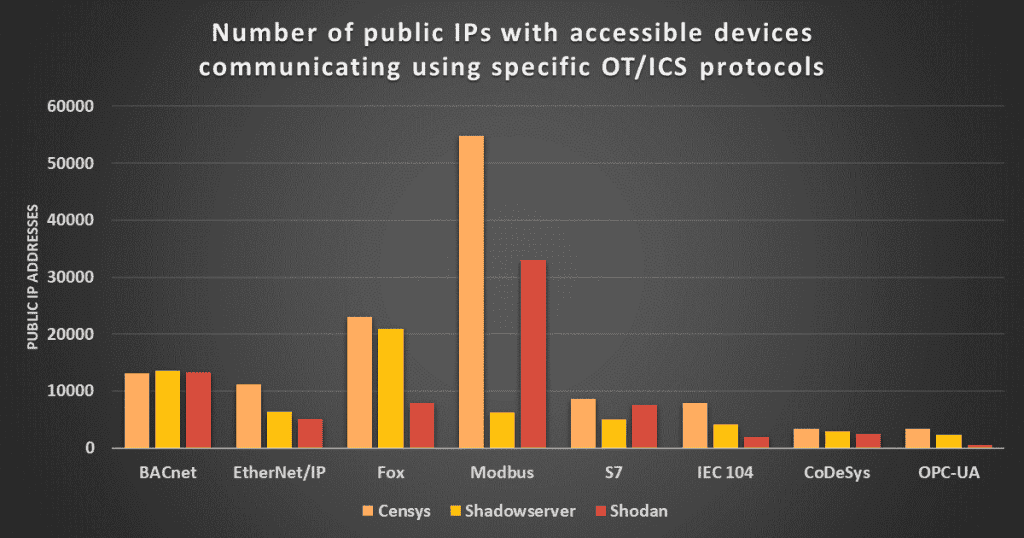
This is broken down further by specific protocol, with Modbus and Fox devices indicated as being the most exposed.
Source: Sans Internet Storm Center
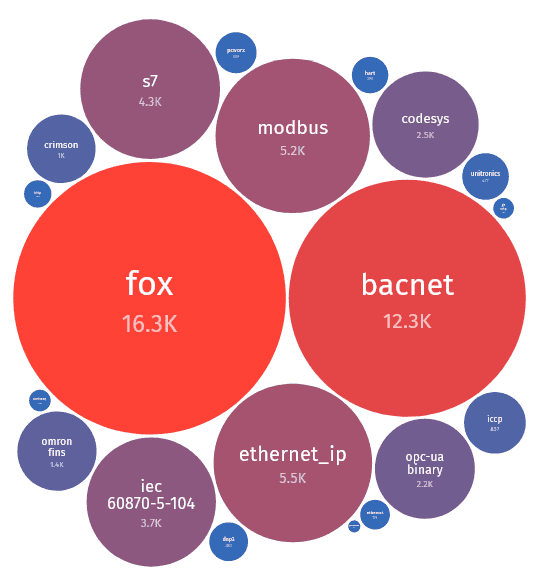
However, this data from ShadowServer indicates that devices using the Fox and BACnet protocols are the most exposed.
Source: ShadowServer
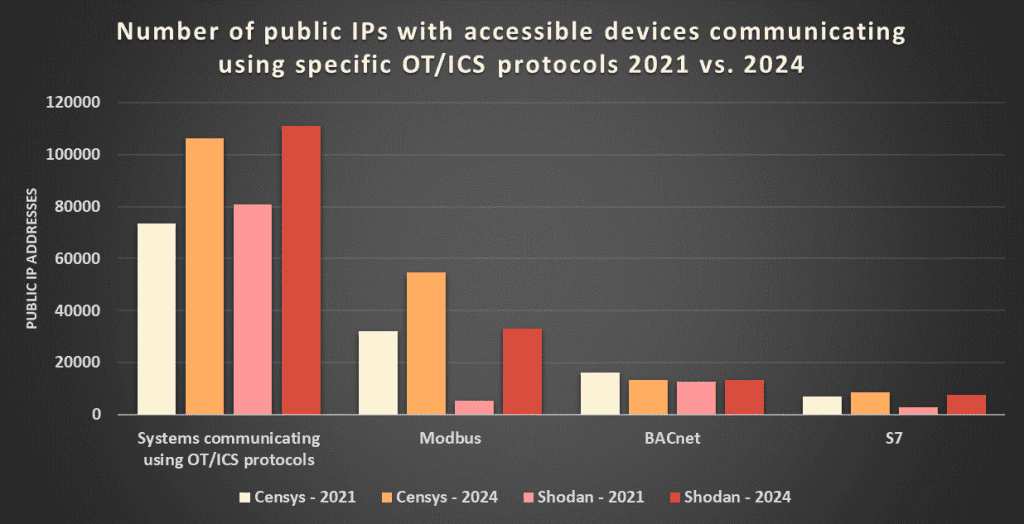
Perhaps most concerning is the growth from 2021 to 2024 of public IP address with devices using OT/ICS protocols. With all of the attention and effort to secure OT/ICS devices, the problem seems to have grown.
Source: Sans Internet Storm Center
Zero Trust for OT/ICS Security
One way to secure exposed OT/ICS devices is to use a zero trust solution that authenticates devices and encrypts data during communication. Through authentication, devices are ensured to only communicate with other approved devices. Veridify’s DOME solution utilizes a NIST-compliant zero trust architecture and can secure both IP-based on non-IP (Modbus RTU, BACnet MS/TP) devices.
—
Blog Post Summary – All of our posts listed on one page back through 2019