Key Differences Between Zero Trust OT Security and Traditional IT Security
How is Zero Trust for OT Security Different from Traditional IT Security?
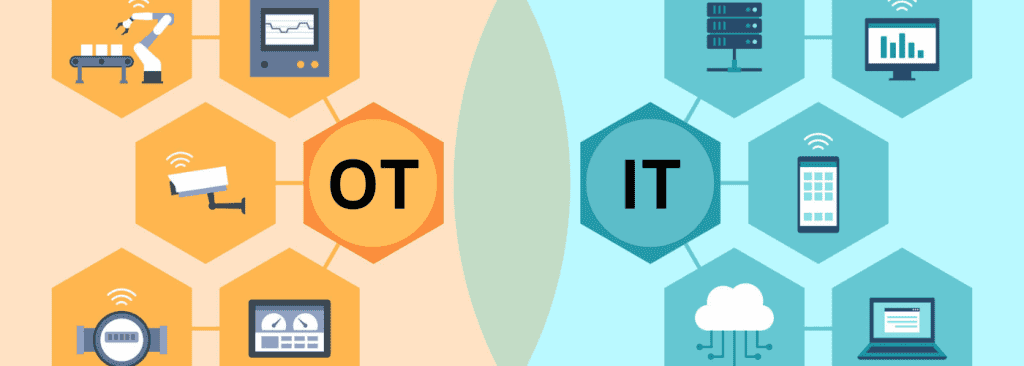
Zero Trust for operational technology (OT) security differs significantly from traditional IT security models in several ways. Here are some key differences:
Security Method |
Traditional IT Security |
Zero Trust OT Security |
| Trust Model | – Assumes that everything inside the network can be trusted.
– Relies heavily on perimeter defenses like firewalls and intrusion detection systems (IDS).
|
– Assumes that no one, whether inside or outside the network, can be trusted by default.
– Requires continuous verification of user and device identities.
|
| Network Segmentation | – Often relies on simple network segmentation, such as VLANs, to separate different types of traffic and devices.
|
– Employs micro-segmentation to create granular zones and restrict access to specific parts of the network.
– Minimizes the attack surface by ensuring that each segment has its own security controls and policies.
|
| Access Controls | – Uses role-based access controls (RBAC) and often grants broad access based on user roles.
|
– Implements strict access controls using principles of least privilege and need-to-know.
– Continuously evaluates access requests using context such as user identity, device health, location, and behavior.
|
| Monitoring and Visibility | – May have limited visibility into OT networks and often relies on periodic security assessments and static configurations.
|
– Provides continuous monitoring and real-time visibility into all network activities.
– Uses advanced analytics and machine learning to detect anomalies and potential threats. |
| Identity and Device Management | – Often lacks robust mechanisms for managing identities and devices, especially in legacy OT environments.
|
– Emphasizes strong identity management, including multi-factor authentication (MFA) and device posture checks.
– Ensures that only authorized and compliant devices can access the network. |
| Response to Threats | – Reactive in nature, responding to threats after they have been detected.
– Relies on signatures and known threat patterns.
|
– Proactive approach that assumes breach and continuously works to minimize potential impact.
– Uses behavioral analysis and anomaly detection to identify and mitigate threats in real-time.
|
| Implementation Approach | – Can be easier to implement initially but may become less effective over time as threats evolve and the network grows more complex.
|
– Requires a more strategic and comprehensive implementation, including modernizing infrastructure and processes.
– Provides a more adaptable and resilient security posture against evolving threats.
|
In Summary
Zero Trust for OT security is fundamentally about ensuring that every access request is verified, monitored, and controlled, regardless of where the request originates. It provides a more robust and dynamic security framework compared to traditional IT security models, which often rely on outdated assumptions about network trust and perimeter defenses.
Keywords: Zero Trust OT Security vs. Traditional IT Security – Key Differences
Related Resources
Blog Post Summary – All of our recent posts listed on one page