Siegeware and the Cyber Defense of Smart Buildings
The Birth of Siegeware
The concept of siegeware emerged around 2017-2018 [1] as a specific cybersecurity threat targeting smart buildings and their automated systems which are also known as operational technologt (OT). The emergence of siegeware as a concept coincided with the rapid growth of smart building technologies and the Internet of Things (IoT) in commercial real estate. As buildings became more connected and reliant on digital systems, cybersecurity experts recognized the potential for malicious actors to exploit these OT systems in ways similar to traditional ransomware attacks on IT systems, but with physical consequences.
Key Aspects of Siegeware
Siegeware is a relatively new cybersecurity threat that specifically targets smart buildings and their automated systems. This term combines “siege” (referring to the act of surrounding and attacking a fortified place) with “ware” (as in malware or ransomware).
Important elements of of siegeware include:
- Target: Smart building systems and Building Automation Systems (BAS)
- Method: Hackers gain control of a building’s digital infrastructure, potentially locking out legitimate users or administrators
- Goal: Usually to extort money from building owners or managers by threatening to disrupt critical building functions
- Potential impacts:
- Disruption of HVAC systems
- Manipulation of access control systems
- Interference with elevator operations
- Control of lighting systems
- Tampering with security cameras and alarms
- Disabling fire safety, life safety, or power management systems
- Vulnerabilities exploited:
- Weak security in Internet of Things (IoT) devices
- Outdated or unpatched building management software
- Poor network segmentation in building systems
- Lack of proper authentication and access controls
- Increasing risk: As buildings become “smarter” and more connected, the attack surface for siegeware expands
- Prevention strategies:
-
- Employee training on cybersecurity best practices
-
Identifying Siegeware Targets
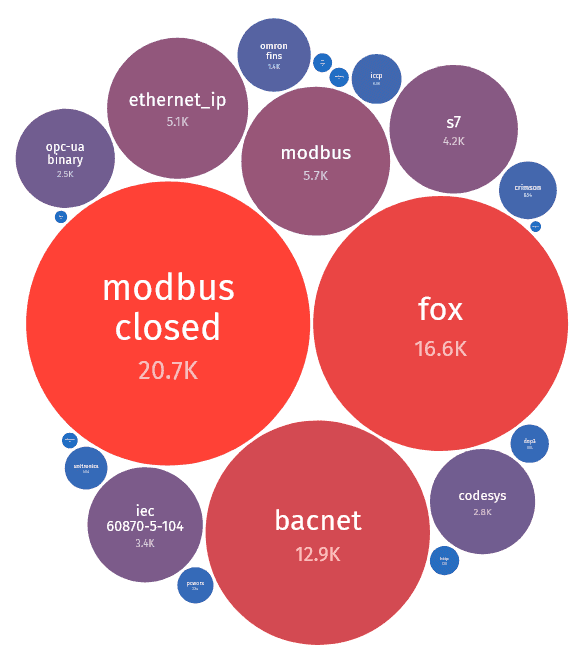
ShadowServer (dashboard.shadowserver.org/#ics-ot) provides a sense of the scale of exposed systems – note that Modbus, Fox, and BACnet (all commonly used in buildings) are the devices with the most aggregate exposure.
Tools such as Shodan (www.shodan.io) and Censys (search.censys.io) make it easy to zero in on exposed devices as potential targets. For a deeper dive into identifying targets, the article “Sharks in the Water” provides an excellent and detailed example of using Shodan and Censys to identify exposed building control devices.
Cyber Defense Against Siegeware
Defending against siegeware requires a multi-layered approach that addresses the unique vulnerabilities of smart building systems. Here are some of the best ways to protect against siegeware attacks:
- Network Segmentation
- Isolate building automation systems from the main corporate network
- Possible use of virtual LANs (VLANs) to separate different building systems
- Zero Trust Authentication
- Ensure that only authenticated building management and control devices can communicate to other similarly authenticate devices
- Implement Strong Access Controls
- Implement multi-factor authentication (MFA) for all users
- Use the principle of least privilege to limit access rights
- Regularly audit and update access permissions
- Regular Software Updates and Patch Management
- Keep all building management software and firmware up-to-date
- Implement a robust patch management process for all connected devices
- Encryption
- Use strong encryption for all data in transit and at rest
- Ensure secure communication protocols are used between devices and systems
- Continuous Monitoring and Threat Detection
- Implement 24/7 monitoring of building systems
- Use intrusion detection and prevention systems (IDS/IPS)
- Employ anomaly detection tools to identify unusual behavior
- Incident Response Plan
- Develop and regularly test a comprehensive incident response plan
- Include procedures for manual override of critical systems
- Employee Training
- Conduct regular cybersecurity awareness training for all staff
- Include specific training on smart building vulnerabilities and siegeware threats
- Vendor Management
- Carefully vet all third-party vendors with access to building systems
- Ensure vendors follow strict security protocols
- Revoke old vendor access privileges when switching to a new vendor
- Regular Security Audits and Penetration Testing
- Conduct frequent security assessments of building systems
- Perform penetration testing to identify vulnerabilities
- Backup and Recovery
- Maintain secure, offline backups of all critical system configurations
- Develop and test recovery procedures for various attack scenarios
- Physical Security
- Secure physical access to critical building control systems
- Implement surveillance and access logs for sensitive areas
- IoT Device Security
- Use secure, enterprise-grade IoT devices when possible
- Change default passwords and disable unnecessary features on IoT devices
Siegeware represents a significant threat to modern smart buildings, potentially causing disruptions to critical infrastructure and posing risks to occupant safety and comfort. Building owners and managers need to be aware of this threat and take proactive measures to protect their systems.
By implementing these protective measures, building owners and managers can significantly reduce the risk of siegeware attacks and enhance the overall security posture of their smart building systems.
References
[1] In 2017 the term “siegeware” was coined by researchers at ForeScout Technologies, a cybersecurity company. In 2018, ForeScout released a report titled “Rise of the Machines: Transforming Cybersecurity Strategy for the Age of IoT,” which introduced the concept of siegeware to a wider audience. In August 2018, the concept gained more attention when researchers demonstrated at the DEF CON hacking conference how they could potentially take control of a building’s systems.
—
Blog Post Summary – All of our recent posts listed on one page