The Importance of Protecting Smart Building Technology from Cyber Threats
Smart Building Technology Market Size
Juniper Research estimates more than 115 million buildings will deploy smart building technologies by 2026, an increase of over 2.5X from 2022. Grandview Research (graph) and Fortune Business Insights both predict CAGR of over 20% through 2030 for the smart building market.
Smart building technology has revolutionized the way buildings are managed, providing greater control and efficiency over critical systems such as heating, ventilation, air conditioning (HVAC), lighting, elevators, life safety, and security. Benefits of deploying smart building technology include:
- operational efficiencies
- improving the quality and convenience of the working environment
- reducing energy consumption
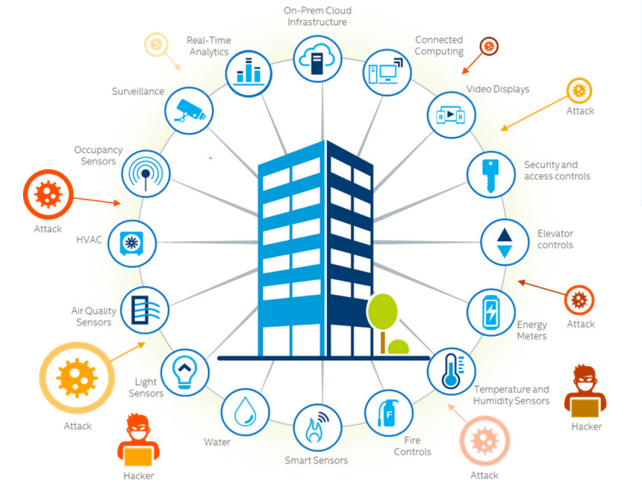
Smart Building Cybersecurity Risks
With increased control, automation, and connectivity comes the need to protect these devices from cyber threats and attacks. Stand-alone devices such as a room-based occupancy or motion sensors that control lights locally are not at risk since they are generally not connected to a network. However, a security breach in a smart building’s connected systems could have serious consequences. For example, an attacker could:
- manipulate temperature and other operational setpoints
- turn on/off fans
- make motors run at higher speeds
- disable notifications, warnings, or alarms
- disable elevators, escalators, and lighting systems
- turn off life safety systems
- cause equipment damage
- disable security systems
The measures can put the safety and security of building occupants at risk. Additionally, a breach could compromise sensitive information, disrupt business operations, and result in significant financial losses.
Smart Building Cybersecurity Protection
To mitigate these risks, it is essential to secure smart building devices. This involves implementing strong security measures, including but not limited to:
Security Program: Creation of a security program that covers governance, policies, and roles for both IT and OT personnel (including contractors).
Asset Inventory: Building an inventory of all of the operational assets and related data such as manufacturer, model numbers, software versions, physical locations, and network address.
Risk Assessment: Documenting when, how, and what was assessed, and associated risk ratings.
Service Provider Management: Documenting the list of service providers, key contacts and authorized personnel, the scope of responsibilities, system permissions, and other information.
Network Security: Solutions such as firewalls help to prevent unauthorized access to a network, and network segmentation to help limit exposure if a breach occurs.
Software Updates: Regular software updates and patches should be applied to address known system vulnerabilities.
Device Security: Devices should be authenticated to each other using a zero trust framework to ensure that device-to-device communications are permitted, and communication should be encrypted to protect data.
System/Network Access Control: Documents who is able to access the network and devices, how they are able to do it, and signed copies acknowledging your remote access policy. Also included should be a documented process for adding and removing users, assigning permissions, and periodic review.
Network Documentation: System drawings on how the network and devices are connected, and related documentation for devices, software versions, network addresses, protocols, VLANs, and ports.
Physical Security: Smart building devices should be physically secured and access to them should be restricted to authorized personnel only. This helps to prevent unauthorized physical access and tampering with the devices, which could compromise their security or enable device spoofing.
System Backup/Restore: Documentation and process for what is being backed up, frequency of backup, how and where backups are stored, and who has access to the backups. Also, documented process for how to restore software and configuration settings.
Change Management: Documentation that describes the process for approval, scheduling, and deployment of changes to the smart building infrastructure.
Training: Staff and contractors should be have security awareness training in order to be able to access the systems that operate the smart building infrastructure
System Security Verification: Documentation that indicates the systems or changes have been deployed and cybersecurity measures have been implemented and tested. Also included should be scheduled for on-going reviews and testing to verify security measures have not been eliminated or altered.
Processes: Security processes should be documented and audited to make sure they are being followed and how to respond in case of a cybersecurity event. Smart building devices should be integrated into the overall security architecture of the building. This includes ensuring that the devices are part of a comprehensive security plan, which includes incident response procedures, regular security audits, and security awareness training for employees.
This is not an exhaustive list, but is indicative of the level of planning, documentation, and processes needed to deploy and maintain robust cybersecurity protection for smart buildings. Protecting smart building devices is crucial to maintain the confidentiality, integrity, and availability of critical information, and to ensure the overall safety and security of the building and its occupants. By implementing strong security measures and regularly reviewing and updating them, organizations can reduce the risk of security breaches, minimize costs, and maintain the reliability and functionality of smart building systems.
—
Blog Post Summary – All of our posts listed on one page back through 2019
See the slides below to learn more about cybersecurity for building controls and smart buildings:
Keywords: smart building technology






