Zero Trust for OT Security: Cyber Defense Inside the Perimeter
Inside the Perimeter Defense is a Crucial Part of Defense in Depth for OT Security
Firewalls for OT Security Perimeter Defense
Firewalls are essential components of network security, acting as perimeter defenses that control incoming and outgoing network traffic based on predetermined security rules. However, they are not without their own set of potential security problems including:
- Misconfigurations (overly permissive rules, incomplete rule sets)
- Outdated firmware (unpatched vulnerabilities, lack of feature updates)
- Complex Rule Sets (overlapping or conflicting rules)
- Insufficient Logging and Monitoring
- Weak Policy Enforcement (policy drift, lack of standardization)
Addressing these typical firewall security problems requires careful planning and regular maintenance. When proper maintenance is ignored security gaps can increase and unauthorized people may be able to get inside the perimeter. Once inside the perimeter, users are typically granted access to all resources as if they were inside the building.
IT-centric Solutions Aren’t Sufficient for OT
What works on an industrial PC or HMI will not likely work on OT field devices with small microprocessors. Conventional antivirus and endpoint detection response (EDR) solutions are problematic to deploy and run on OT endpoints – especially ones that don’t have an operating system – and are no longer sufficient to protect your OT networks with today’s threats. These tools only address “known” identified threats where a method to block them has already been developed and deployed. They are powerless to guard against unforeseen threats that exploit unknown application vulnerabilities, nor do they prevent never-seen-before (zero day) attacks on day zero.
Cybercriminals are exploiting these gaps in protection to deploy the harmful malware/ransomware and fileless intrusion attacks against critical OT infrastructure. The emergence of AI-driven methods is further accelerating the frequency and severity of attacks, forcing security teams to be responsive rather than proactive. While current antivirus and EDR solutions can detect and prevent the known threats, cybersecurity personnel must prepare for the unexpected.
Guarding Against The Unknown Inside the Perimeter
How do you guard against unknown threats? There are lots of common ways to monitor and look for anomalies on a network or within devices, but if human action is required to analyze, respond, and remediate, then this is passive protection that can result in bad operation and safety outcomes. Active protection stops incidents in real-time, without human intervention, leaving operations uninterrupted and personnel safe.
Guarding against unknown cyberattack methods, often referred to as “zero-day attacks,” requires a proactive and multi-layered approach to cybersecurity. Since these attacks exploit vulnerabilities that are not yet known, traditional defenses like signature-based antivirus software may not be effective.
Defense Inside the Perimeter
When a firewall is breached, the intruders are inside the perimeter. Defending against these intruders is more difficult since they theoretically have access to all network resources unless they are limited by some implementation of network segmentation. However, even access to a network segment can lead to undesired snooping, operational disruption, malware infestation, or data extraction. A key method for cyberdefense inside the perimeter is a security method based on zero trust.
Zero Trust OT Security
Zero Trust is different than traditional IT security and this is covered in this related post.
Zero Trust is a proactive security framework that no longer assumes trust should be given once network access has been achieved (or breached). By definition, zero trust assumes that communications from all devices are untrustworthy unless authenticated. This is not a one-time authentication to gain resource access, authentication must be continuous. Four major tenants of the US Department of Defense Zero Trust Reference Architecture include:
- Assume a hostile environment
- Presume breach
- Never trust, always verify
- Scrutinize explicitly
The architecture assumes that threats exist both inside and outside the network. It treats every access attempt as potentially malicious, regardless of the source. Users, devices, and applications are granted the minimum level of access necessary to perform their functions, reducing the potential impact of a security breach. Continuous monitoring and real-time verification of users, devices, and application states are required before granting or maintaining access to resources.
Implementing Zero Trust for Legacy OT Devices
Zero Trust for OT security is fundamentally about ensuring that every access request is verified, monitored, and controlled, regardless of where the request originates. For legacy OT devices that are not capable of being updated with the latest security methods, and overlay approach to zero trust security can provide the protection externally.
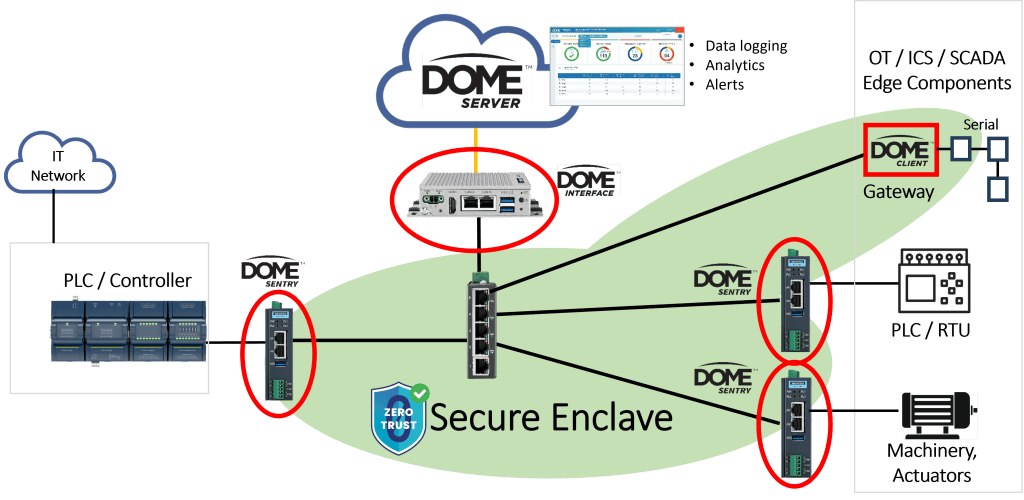
Legacy devices protected by DOME can participate in a secure enclave based on zero trust. In the diagram below, zero trust security is provided with an overlay approach that results in no changes to the network, and it is completely transparent to the existing devices.
DOME Sentry devices are used to implement the zero trust security and do not directly communicate to the internet for continued security. Cloud communication is handled through the DOME Interface Appliance (DIA).
- DOME provides the following key functions:
- Authenticates DOME Sentry devices to the network
- Authenticated DOME Sentry devices to each other to create a secure enclave
- Encrypts data from OT devices
- Authenticates and decrypts each packet from other OT devices
- Blocks, records, and alerts all communication attempts from unauthenticated devices
The result is that cyberattacks are stopped in real-time before even reaching the desired target device.
—
Blog Post Summary – All of our recent posts listed on one page