Renesas and Veridify Security have joined forces to deliver strong security solutions, Public Key authentication and identification for RA, RE, RX and RL78-based devices. Now Renesas customers will be able to quickly and easily secure these devices at the edge of the IoT. Veridify’s methods are extremely efficient – delivering fast performance, a small footprint and ultra-low energy consumption making them ideal for sensor-based platforms where energy or battery life may be an issue. There are no databases or active network connections required to run our security methods. And for products that will be in the field for more than five years, our solutions are future proof – resistant to all known quantum attacks. SDKs and tools are available now to easily and quickly integrate our methods into your solutions.
Securing RA, RE, RX and RL78 Devices at the Edge of the IoT
The extraordinary growth of the Internet of Things (IoT) has given rise to a problem. While we all enjoy the convenience associated with our connected devices, nearly every day we can read about compromised cars, IoT devices, and the vulnerability of our infrastructure. The partnership between Renesas and Veridify addresses the challenges of securing products at the edge of the IoT.
View detailed RA2 security solution information
View the RA6 Security Demonstration video
View Renesas RE partner solutions
View the RE01 Series Solution Brief
View the RX100 Series Solution Brief
View the RX130 SDK Getting Started Guide
Learn more about the Renesas and Veridify Security collaboration
Public-key Cryptography for the RL78
Private-key(symmetric) security methods like AES are available today on the RL78 and provide a solid solution for encrypting data. But scalability in the IoT becomes a challenge due to the difficulty in securely distributing keys. As a result, a single breach can bring down an entire solution. Public-key (asymmetric) methods solve the challenge of securely distributing keys, but legacy Public-key methods based on Elliptic Curve Cryptography (ECC) and RSA too computationally intensive to deliver a practical solution for 16-bit devices like the RL78.
In contrast, Veridify's computationally efficient Public-key methods, based on Group Theoretic Cryptography, have much smaller RAM/ROM requirements and easily run on 16-bit processors like the RL78, in software, without accelerators or additional processor support. (If you are interested in the mathematics of Group Theoretic Cryptography, see our white papers and technical papers here.)
If you are developing a product with a lifespan of five or more years, you may be concerned about security threats from quantum computers. The National Security Agency has issued a warning that quantum computing will break legacy methods like ECC and RSA. SecureRF's cryptographic methods are quantum-resistant to all known attacks and will secure your RL78-based devices well into the future.
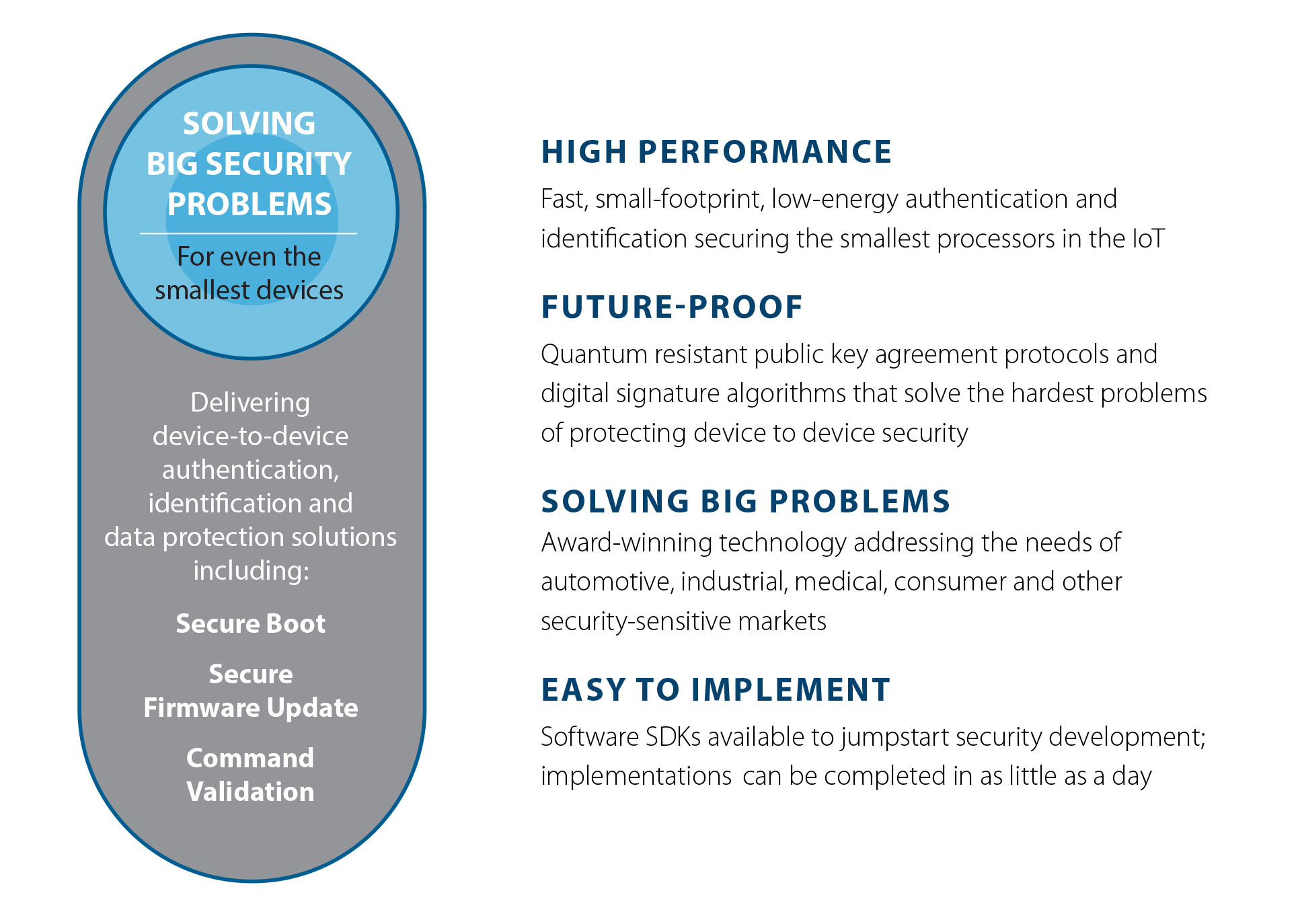
IoT Security Solutions for the Renesas RL78
Veridify has packaged two of its methods for deployment on the Renesas RL78: our Ironwood Key Agreement Protocol (Ironwood KAP) and Walnut Digital Signature Algorithm (WalnutDSA).
Ironwood KAP allows two devices to create a shared secret without prior communications. It has been optimizedfor the security needs of the RL78. In benchmark tests, it performed 60 times faster than ECC.
WalnutDSA allows rapid verification of a data element, which can be used to validate a digital entity or data content. We have run WalnutDSA at speeds as much as 90 times faster than ECC.
With these two methods and our tools, engineers can provide device-to-device authentication, identification, and data protection solutions including Secure Boot, Secure Firmware Updates and Command Validation to ensure trusted communications between the RL78 and other devices.
Ready to find out more?
Contact us to speak with an IoT security expert.